How healthcare providers should respond to a HIPAA incident depends on the type of incident, how it was caused, what the impact is, and whether additional measures could be implemented that mitigate the risk of a recurrence – or mitigate the risk of an unimpactful HIPAA incident deteriorating into something more serious.
In theory, the term “HIPAA incident” could apply to any event that violates a HIPAA Administrative Simplification Regulation. For example, a coding error that results in a Medicare over-payment could be referred to as a HIPAA incident, as could an unattested verbal disclosure of reproductive health information that violates the HIPAA Privacy Rule.
However, the only definition of a HIPAA incident appears in the HIPAA Security Rule – §164.304 of the HIPAA Security Rule stating “Security incident means the attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system”.
The takeaway from this definition is that it applies to unsuccessful attempts to access Protected Health Information (PHI) and the systems on which PHI is stored as well as successful attempts. The reason for this, and why healthcare providers should respond to a HIPAA incident that is unsuccessful, is explained later in this article.
A HIPAA Incident is Not Necessarily a HIPAA Data Breach
There are generally three types of HIPAA incident – unsuccessful attempts to access PHI that are prevented by a security measure outside the network (i.e., by an email filter), unsuccessful attempts to access PHI that are prevented by a security measure within the network (i.e., by anti-virus software), and successful attempts that gain unauthorized access to PHI.
Only the third type of HIPAA incident qualifies as a HIPAA data breach – and, only then, if the unauthorized access has resulted in unsecured PHI being acquired or compromised. In these circumstances, how healthcare providers should respond to a HIPAA incident can depend on several factors, including:
Was the unauthorized access attributable to the actions of an internal or external actor?
While headline data breaches are most commonly associated with the actions of external actors, 80% of all data breaches in healthcare include a human element. The human element may consist of actions that allow access to external actors – for example, an interaction with a phishing email or the misconfiguration of a cloud server – but is more likely to consist of a miscellaneous error such as sending PHI to the wrong recipient or the loss of a device.
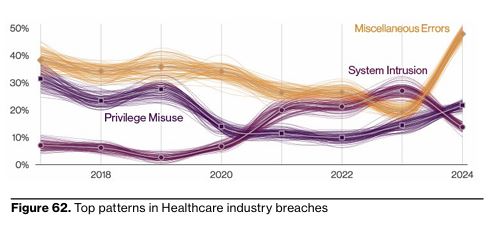
Unauthorized access is most likely attributable to a miscellaneous (human) error. Source: Verizon DBIR Report 2024
Did the unauthorized access involve the misuse or acquisition of login credentials?
The second most common cause of HIPAA incidents is snooping. This is when a member of the workforce misuses their login credentials – or acquires the login credentials of a colleague – to access the medical records of family members, friends, colleagues, or celebrities. While most snooping is attributable to inquisitiveness, accessing a patient’s medical records for purposes not permitted by the HIPAA Privacy Rule is a violation of HIPAA and a notifiable data breach.
Is the HIPAA incident ongoing, and – if so – what can be done to prevent its spread?
Several sources recommend disconnecting compromised devices, disabling user accounts, or isolating affected systems when a HIPAA incident is ongoing to prevent its spread. However, when healthcare providers respond to a HIPAA incident in this way, it is first important to establish that the devices or systems are not critical to patient care. In all circumstances, the continuity of care must take priority over responding to a HIPAA incident.
Do law enforcement agencies need to be alerted to the incident?
If a HIPAA security incident is due to a malicious insider knowingly obtaining, disclosing, or causing a disclosure of PHI in violation of §1177 of the Social Security Act, or if a HIPAA security incident is attributable to the presence of ransomware, it is necessary to alert law enforcement agencies to the incident. If a law enforcement investigation results in a delay in notifying the breach, it is advisable to acquire a written notice of delay from the law enforcement agency.
Would additional measures mitigate the risk of a recurrence?
A common reaction to a HIPAA incident is to add further security measures. However, considering that 80% of data breaches in healthcare have a human element, additional security measures are likely to have minimal effect. A better response to a HIPAA incident is to increase the amount of HIPAA training provided to workforce members – particularly HIPAA training that focuses of consequences of data breaches such as identity theft, operational disruptions, etc.
Why Respond to Unsuccessful HIPAA Incidents
Healthcare providers should respond to a HIPAA incident that is unsuccessful because it may be an indication of an attack type that increases in intensity over time and ultimately leads to a successful intrusion into a healthcare provider’s network. Examples include phishing emails blocked by an email filter and malware quarantined by anti-virus software.
Monitoring reports produced by security solutions can help identify trends in attack types so that, when a trend is identified, healthcare providers can respond to a HIPAA incident that is not yet successful by implementing further security measures, reconfiguring existing security measures to address the threats, or re-focusing workforce training on new attack vectors.
Increasing – or re-focusing – workforce training is particularly relevant to how healthcare providers should respond to a HIPAA incident that is unsuccessful when an attempt to access PHI has been prevented by the diligence of a workforce member. It may be the case that, if the attempt had targeted a less diligent workforce member, the attempt may have been successful.
Furthermore, identifying and responding to suspected and unsuccessful HIPAA incidents is not only a best practice for healthcare providers. It is a requirement of the HIPAA Security Rule (§164.308) that healthcare providers conduct and document these tasks to mitigate the likelihood of a HIPAA incident being successful and any harmful effects of the incident.
How to Plan for a HIPAA Incident Response
Due to the different nature of threats, the different types of healthcare providers, and the HIPAA Security Rule’s technical neutrality and flexibility of approach, there is no one-size-fits-all plan for a HIPAA incident response. However, the following core components can be used by healthcare providers to customize their own HIPAA incident response plans:
Preparation and Communication
- Develop policies and procedures for each type of reasonably anticipated incident.
- Document which types of HIPAA incidents should be escalated, and who to.
- Provide training to workforce members on how to respond to a HIPAA incident.
- Ensure policies, procedures, documentation, and training is constantly available.
Detection and Identification
- Configure existing security measures to detect anomalies in network and system behavior.
- Implement further measures as necessary to secure the network perimeter and mobile devices.
- Schedule reviews of audit logs and access reports to manually detect additional anomalies.
- Clearly outline what types of activity warrant a HIPAA incident response and by who.
Analyze, Contain, Respond, and Recover
- Analyze the consequences of taking specific actions before responding to any HIPAA incident.
- Subject to the analysis, select the most appropriate method to contain a successful intrusion.
- Plan how the organization will respond to the internal and external causes of different incidents.
- Plan how affected systems and information will be restored to minimize the risk of recurrence.
Post-Incident Activities
- Have procedures in place in to inform law enforcement where necessary and issue breach notifications.
- Conduct a lessons-learned review to examine how the incident was detected, reported, and responded to.
- Revise the plan for a HIPAA incident response, document the changes, and provide further workforce training.
- Test the revised plan for a HIPAA incident response through tabletop exercises and simulated breach scenarios.
The Advantages of HIPAA Incident Response Software
Planning for a HIPAA incident response and responding to a HIPAA incident is time consuming and can be subject to human error, evolving incident types, and changing regulations. However, there are various types of HIPAA incident response software healthcare providers can take advantage of to better plan for a HIPAA incident response or to respond to a HIPAA incident.
Generally, HIPAA incident response software ranges in capabilities from document portals that ensure policies, procedures, and response plans are constantly available to SOAR (Security Orchestration, Automation, and Response) platforms that automatically trigger predefined workflows when a HIPAA incident is detected (i.e., blocking suspicious network traffic).
While the most advanced HIPAA incident response software would likely prevent many types of HIPAA incident – and would help organizations identify trends in unsuccessful intrusion attempts – the cost and complexity of advanced platforms with SOAR capabilities is hard to justify for smaller healthcare budgets with smaller attack services and limited resources.
Consequently, healthcare providers are advised to review the HIPAA Security Rule’s flexibility of approach standard (§164.306(b)), conduct a risk analysis to identify reasonably anticipated threats, and approach vendors that offer HIPAA incident response software with the capabilities necessary to reduce identified threats to a reasonable and appropriate level – requesting a demo of the software where available.

