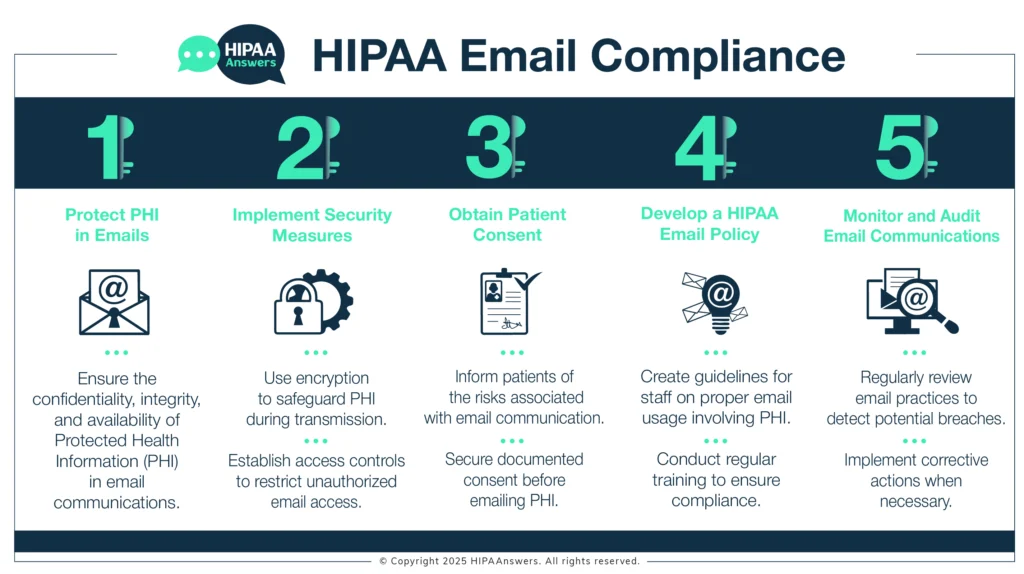
HIPAA compliant email is email containing Protected Health Information that is sent for a purpose required or permitted by the HIPAA Privacy Rule and – when necessary – that is protected by the safeguards of the HIPAA Security Rule. There can be other criteria that determine whether an email complies with HIPAA – including who has requested the email, where the email server is located, and any further conditions or exceptions that apply.
Individuals and organizations that qualify as HIPAA covered entities or business associates are required to ensure emails are HIPAA compliant when they contain Protected Health Information (PHI). In most circumstances, this means that the purpose for sending an email must be a purpose required or permitted by the HIPAA Privacy Rule, and that the security of PHI in – or attached to – an email is protected by the safeguards of the HIPAA Security Rule.
However, there are many conditions and exceptions that can apply to the HIPAA email rules. These may be due to individuals exercising their HIPAA rights, organizations adopting a flexible approach towards HIPAA compliance, or state laws that preempt HIPAA. It is not possible to review every possible scenario for HIPAA compliant email, and this article discusses those which occur most often and raise most questions about the HIPAA email requirements.
The Privacy Rule HIPAA Email Requirements
Individuals Rights under HIPAA and Email
Disclosures of PHI to Business Associates
The HIPAA Security Rule and HIPAA Email Compliance
Applicability, Flexibility, and Addressability
Why the Location of the Mail Server Matters
The HIPAA Encrypted Mail Requirements
The Standards for HIPAA Compliant Encrypted Email
Alternatives to the HIPAA Email Encryption Requirements
Other Considerations for HIPAA Compliant Email
State Laws & Notices of Enforcement Discretion
Workforce Training and HIPAA Sanctions
Why is it Important Email is HIPAA Compliant?
The Privacy Rule HIPAA Email Requirements
The HIPAA Privacy Rule governs which uses and disclosures of PHI are required and permitted – by email or by any other means. Required disclosures of PHI include disclosures to HHS’ Office for Civil Rights to respond to complaints and compliance investigations, and to the subjects of the PHI (i.e., plan members, patients, authorized personal representatives, etc.) when they exercise their HIPAA rights to request a copy of PHI or transfer PHI to a different covered entity.
Permitted disclosures of PHI include disclosures for treatment, payment, and health care operations, disclosures required by law, and disclosures to business associates. Other than disclosures for treatment purposes and some disclosures required by law, all permitted disclosures are subject to the minimum necessary standard. Disclosures relating to reproductive health care are also subject to the attestation requirements of §164.509.
Individuals Rights under HIPAA and Email
In addition to the rights to request copies of PHI and transfer PHI to a different covered entity, patients have the rights to request PHI (or some elements of PHI) are withheld from third parties, request confidential communications by email, and authorize disclosures of PHI that are otherwise not permitted by the Privacy Rule. When requests and authorizations are “reasonable” and valid, covered entities are required to accommodate them.
The right to withhold PHI from third parties makes it more important that covered entities and business associates comply with the verification requirements of §164.312(d), while the rights to request confidential communications by email and authorize disclosures override the Security Rule requirements for HIPAA compliant email if the individual making the request is warned of the risks of unsecured email and decides to proceed with the request regardless.
Disclosures of PHI to Business Associates
Disclosures of PHI to business associates – and by business associates to subcontractors – are permitted by the HIPAA Privacy Rule provided a Business Associate Agreement exists between the two parties. The Business Associate Agreement must establish the permitted uses and disclosures of PHI shared with the business associate and stipulate that the business associate will comply with all applicable standards of the Privacy and Security Rules.
Although the Final Omnibus Rule made business associates directly liable for HIPAA violations and data breaches due to a lack of HIPAA compliance, covered entities are still required to monitor business associates’ compliance and terminate Agreements if there is evidence to suggest the business associate is not complying with the Agreement, the applicable standards of the Security Rule, or any other HIPAA standards that apply to the Agreement.
The Security Rule and HIPAA Email Compliance
Other than when the Security Rule requirements for HIPAA compliant email are overridden by an individual exercising their HIPAA rights, the Security Rule governs what Safeguards must be in place to protect the confidentiality, integrity, and availability of PHI at rest (i.e., in an email inbox) and in transit (i.e., between a covered entity and a business associate). The Safeguards for protecting PHI at rest and in transit fall into three categories – Administrative, Physical, and Technical.
· The PHI Email Administrative Safeguards
The PHI email Administrative Safeguards require covered entities and business associates to conduct a risk analysis to identify threats to PHI in emails created, received, stored, and transmitted by the organization. Measures must be implemented to mitigate the risks from identified threats (i.e., malware protection) and to monitor and review system activity.
The same Safeguards require all workforce members to participate in a security awareness training program. Phishing susceptibility testing is now recommended by HHS to mitigate the threat from phishing emails. In addition, the PHI email Administrative Safeguards require organizations to develop contingency plans to ensure the availability of PHI in an emergency.
· The PHI Email Physical Safeguards
The PHI email Physical Safeguards govern the security of the facilities in which hardware is stored, the security of devices used to access PHI, and how devices – including removable storage volumes on which PHI is stored – should be decommissioned when no longer required. They Safeguard also govern the security of facilities, servers, and devices during maintenance.
Many of the PHI email physical safeguards will not apply to organizations that use cloud-based email services such as Outlook and Workspace Gmail because the service provider has the responsibility for the security of facilities and servers. However, organizations will still be responsible for the physical security of workplace devices and workforce mobile devices.
· The PHI Email Technical Safeguards
The PHI email Technical Safeguards for HIPAA compliant email require covered entities and business associates to implement measures to limit access to PHI stored in emails, ensure that PHI stored in emails is not improperly altered or deleted, and encrypt PHI when it is at rest and in transit (the HIPAA encrypted email requirements are discussed below).
The measures that have to be implemented include unique user authentication, emergency access procedures, and audit controls to examine activity in users’ email accounts. Most other PHI email technical safeguards are subject to the results of a risk assessment. These include automatic logoff and a mechanism to authenticate the integrity of PHI (i.e., an email archive).
Applicability, Flexibility, and Addressability
It was mentioned in the introduction to this article that PHI has to be protected by the safeguards of the HIPAA Security Rule “when necessary”. The “when necessary” comment most often applies to scenarios in which individuals exercise their HIPAA rights to request PHI by email when there is no HIPAA compliant email service in place. It can also apply due to the applicability, flexibility, and addressability standards of the HIPAA Security Rule.
· The Applicability Standard
The applicability standard (§164.302) states covered entities and business associates must comply with the applicable standards of the Security Rule – not all of the standards. It has already been mentioned that some PHI email physical safeguards do not apply to organizations that use cloud-based email services. There may be other standards that do not apply to HIPAA email compliance depending on how PHI is communicated with third parties.
· The Flexibility Standard
The flexibility standard (§164.306(b)) allows covered entities and business associates to decide what measures to implement in order to comply with the HIPAA email requirements based on factors such as the size of the organization, its security capabilities, and the cost of implementing the measures. In theory, an organization could claim that it did not implement a security measure because its IT team did not have the capabilities to manage it.
· The Addressability Standard
The addressability standard (§164.306(d))explains that some implementation specifications are required, while others are addressable. Organizations can replace addressable implementation specifications with equivalent measures or omit them completely if a risk assessment determines they are not reasonable and appropriate for protecting the confidentiality, integrity, and availability of PHI created, received, maintained, or transmitted by email.
Why the Location of the Mail Server Matters
The location of the mail server matters because – as previously discussed – if an organization subscribes to a cloud-based email service, the service provider is responsible for complying with some physical HIPAA compliance email rules. It can also be the case that if a mail server is located on-premises, but the mail service is provided by a third party (i.e. Exchange 2019 or a Managed Service Provider), the third party takes responsibility for the security of PHI in transit.
In all cases in which an email service is not hosted and/or managed on-premises (assuming the HIPAA Security Rule applies), it is necessary to enter into a Business Associate Agreement with third party service providers when PHI is transmitted by email. This applies even when emails are encrypted before being sent using a HIPAA compliant encryption service (i.e., Paubox) and even though the email service provider is unable to view the content of emails.
The HIPAA Encrypted Email Requirements
The HIPAA encrypted email requirements – §164.312(a) for PHI at rest and §164.312(e) for PHI in transit – are addressable implementation specifications. However, if an organization sends, receives, maintains, or transmits PHI in emails other than when an individual exercises their HIPAA rights, it is difficult to conceive of a scenario in which the implementation of encryption or an equivalent alternative is not a reasonable and appropriate measure to protect PHI.
There are various ways in which covered entities and business associates can comply with the HIPAA encrypted email standards. If the mail server is on premises, organizations can create mail flow rules to encrypt emails or use a HIPAA compliant email encryption service. Organizations that subscribe to cloud-based email services will usually find HIPAA compliant encryption is included in enterprise plans or can be purchased as an optional add-on.
The Standards for HIPAA Compliant Encrypted Email
In July 2013, HHS’ Office for Civil Rights published guidance to help covered entities and business associates determine when a breach of PHI was a notifiable breach. The guidance included the standards for HIPAA compliant encrypted email which would render PHI unusable, unreadable, or indecipherable to unauthorized individuals – and thereby not notifiable. The guidance has been adopted as the minimum encryption standards for HIPAA compliant email.
To ensure PHI at rest is unusable to a hacker, HHS’ Office for Civil Rights requires covered entities and business associates to encrypt PHI to the standards of NIST SP 800-111 (AES-128 or higher). With regards to PHI in transit, the guidance provides several options – either a “valid encryption processes for data in motion are those which comply with NIST SP 800-52” (TLS 1.2 or higher) or “others which are FIPS 140-2 validated” (for example, OpenPGP or S/MIME).
Alternatives to the HIPAA Email Encryption Requirements
Although HHS’ Office for Civil Rights acknowledges that the HIPAA email encryption requirements are not mandatory it is difficult to find an equivalent alternative that is equally as effective and that doesn’t require a high level of skill to implement. Common alternatives to HIPAA compliant email encryption include tokenization and pseudonymization. However, at present, Blockchain is not a HIPAA compliant email solution for encryption.
The challenge with solutions such as tokenization and pseudonymization are that the recipients of tokenized and pseudonymized emails have to have a way to convert anonymized PHI back into its original state to be able to access the data. Some systems and networks that are set up for encryption may be incompatible with alternatives to the HIPAA email encryption requirements – neutralizing the equivalency of the equivalent alternative.
Other Considerations for HIPAA Compliant Email
Most other considerations for HIPAA compliant email are situation specific. For example, a healthcare facility that specializes in reproductive health care located in State A may have to be more conscious of disclosing PHI via email than a similar healthcare facility located in State B. Alternatively, a publicly funded school that provides both HIPAA-covered medical services and FERPA-covered medical services may have to isolate two types of designated record sets.
Events in the “other considerations” category most likely to impact HIPAA compliant mail include state laws, notices of enforcement discretion, workforce training, and HIPAA sanctions – both for covered entities and business associates that fail to comply with the HIPAA compliant email requirements, and for members of the workforce that fail to comply with workplace HIPAA email policies, or that access PHI “out of scope” of their function with the covered entity.
State Laws & Notices of Enforcement Discretion
State laws are evolving all the time; and, although many exempt covered entities and business associates, not all do. A recent development in state laws is the requirement to affirmatively opt-in before a covered entity can “process” an individual’s email address. Previously, it was safe to assume that if a patient contacted a provider by unsecured email, it was permissible to reply and send PHI via unencrypted email. This may no longer be the case in some states.
With regards to notices of enforcement discretion, these are notices issued by HHS’ Office for Civil Rights during a local or national emergency event that waive enforcement action for certain types of non-compliant activities. For example, during the COVID-19 public health emergency, enforcement action was waived against business associates who disclosed PHI for public health oversight purposes when this was not permitted by a Business Associate Agreement.
Workforce Training and HIPAA Sanctions
Implementing – or subscribing to – a HIPAA compliant email service and configuring the service to support HIPAA email compliance is not sufficient to guarantee compliance with the HIPAA email rules. All members of the workforce must be trained on how to use the service in compliance with the HIPAA Privacy and Security Rules, how to avoid interacting with phishing emails, and how to report disclosures of their email login credentials.
Covered entities and business associates that identify workforce weakness as a threat to the security of PHI and then fail to mitigate the threat can pay a heavy price. In December 2023, the Lafourche Medical Group agreed to settle allegations that it failed to protect PHI against phishing emails for $480,000. Workforce members can also be sanctioned for failing to comply with HIPAA email policies, or imprisoned if their actions are out of scope of their workplace functions.
Why is it Important Email is HIPAA Compliant?
Approximately 25% of all data breaches affecting more than 500 individuals notified to HHS’ Office of Civil Rights (including Archived notifications) mention email. Having a HIPAA compliant email service and using it in compliance with the HIPAA email rules reduces the likelihood of a notifiable data breach. This has the benefits of:
- Increasing patients’ trust in healthcare providers,
- Encouraging workforces to be more HIPAA aware, and
- Reducing the likelihood of a lawsuit being filed by affected individuals.
The absence of HIPAA data breaches helps build patient trust in healthcare providers. When patients trust that their sensitive information will remain confidential, they are more willing to disclose sensitive information to providers. With more information, providers can make more accurate diagnoses and prescribe more appropriate courses of treatment – which results in increased patient compliance, fewer hospital readmissions, and better patient outcomes.
Most workforce members will have used personal email accounts prior to joining a healthcare workforce and are likely to have developed some bad security habits. Effective HIPAA compliant email training will enable workforce members to identify healthy email security practices and apply the healthy security practices to other elements of their roles – potentially further reducing the likelihood of a HIPAA data breach and maintaining patients’ trust.
The financial consequences of non-compliance with the HIPAA email rules are often portrayed as “comply or be fined”. However, most people familiar with HIPAA enforcement actions will be aware that HIPAA data breaches are rarely resolved with civil monetary penalties. The most common consequences of HIPAA breaches are technical assistance, additional security measures, and workforce training. However, there can be financial consequences from other sources.
In 2009, the HITECH Act gave State Attorneys General the authority to file civil actions against organizations that violated the HIPAA email rules. In recent years, there has also been an increase in class action lawsuits being filed against HIPAA covered entities – not for HIPAA violations, but using HIPAA as a benchmark for the standard of care to protect PHI. Covered entities that suffer an avoidable data breach due to the failure to adopt a HIPAA compliant email service, could face much larger financial consequences than being fined by HHS’ Office for Civil Rights.
HIPAA Compliant Email: Conclusion
Because of the multiple HIPAA complaint ways in which covered entities and business associates can create, receive, maintain, or transmit PHI other than email, not every organization has to comply with the HIPAA email rules. For organizations that do have to comply with the HIPAA email rules, it is important that a HIPAA compliant email service is implemented, configured, and used in compliance with the HIPAA email requirements.
Covered entities and business associates with concerns about whether their existing email systems comply with the HIPAA email requirements – or who lack the resources to configure their systems and train their workforces for HIPAA email compliance – are advised to seek advice from a compliance expert. The benefits of a HIPAA compliant email service can far outweigh the costs of implementation, configuration, and training – and advice if required.